
The main issues of industrial information security
In today’s rapidly developing industrial manufacturing industry, the situation of industrial information security is becoming increasingly severe, and security risks continue to rise. The main problems currently faced by China’s industrial information security include insufficient security awareness, weak technical protection measures, shortage of professional talents, incomplete regulatory standards, inadequate management systems, supply chain security risks, challenges brought by the application of new technologies, incomplete emergency response mechanisms, and insufficient cross industry collaboration. The existence of these problems makes industrial control systems vulnerable to network attacks, threatening production safety and data integrity. It is necessary to strengthen the construction of security protection and management systems, and rapidly improve the ability to ensure industrial information security.
Refined property rights confirmation ensures safety
With the launch of PITreater, users can manage access to factories and machinery, allowing all relevant personnel to only access and operate equipment within their authorized scope, thereby helping users obtain mechanical and information security functions. PITreater can cover a wide range of permissions, from simple activation and user authentication to complex permission matrices and company specific codes. PITreater’s permission management can achieve secure operation mode selection and control access permissions for factories and machines, preventing incorrect operations and illegal manipulation. Both personnel and machines can be protected, and the mechanical and information security of the factory can be effectively strengthened.
With the launch of PITreater, users can manage access to factories and machinery, allowing all relevant personnel to only access and operate equipment within their authorized scope, thereby helping users obtain mechanical and information security functions. PITreater can cover a wide range of permissions, from simple activation and user authentication to complex permission matrices and company specific codes. PITreater’s permission management can achieve secure operation mode selection and control access permissions for factories and machines, preventing incorrect operations and illegal manipulation. Both personnel and machines can be protected, and the mechanical and information security of the factory can be effectively strengthened.

Efficient permission management software
With the release of PITreater, Pilz Pilz has simultaneously launched efficient PITreater management software PIT Translator Manager and PIT User Authentication Service. Users can use PIT Translator Manager to configure PITreater and permission keys, assign user information to each key, and store all user data in the database. In this way, users can have a very clear understanding of the information of the permission key owner.
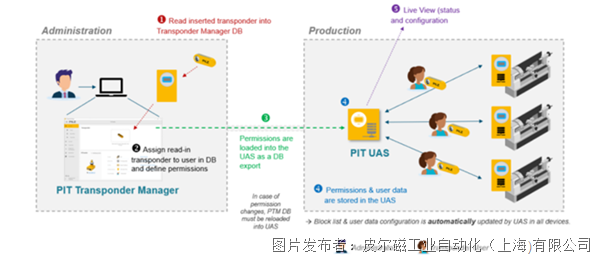
When multiple PITreaters are used simultaneously, users can synchronize the database containing permission information to all PITreaters through PIT User Authentication Service, making configuration more convenient and greatly improving work efficiency.
With the continuous development of intelligent manufacturing and the continuous improvement of industrial ecology, the industrial scale has exceeded one trillion yuan, driving the improvement of social and economic benefits. With the rapid development of industrial Internet, we also need to recognize the importance of industrial Internet security protection, and we need to pay attention to and take corresponding security protection measures in a timely manner.







Leave a comment
Your email address will not be published. Required fields are marked *